Existing software based firewall and QoS applications are insufficient to
meet the ever growing performance and security demands. While today's networks
approach OC-192 (10 Gbit/sec), linear packet filters are already swamped with
handling 1 Gbit/sec even for tiny rulesets. Using powerful, expensive hardware
does not solve the problem since the linear packet classification approach
simply does not scale with the number of rules.
HiPAC focuses on three main aspects forming the basis of today's and future
packet classification applications: performance, scalability
to large rulesets and dynamic rulesets.
In the following, several interesting applications are presented illustrating
that all these aspects are becoming more and more important.
Object based ruleset representation in management front-ends
Most modern firewall front-ends base their ruleset representation on network
objects, i.e. each rule consists at least of a source, destination and service
object where the source/destination object is a collection of IP addresses
and networks and the service object is a collection of ports and port ranges.
This representation is intended to increase maintainability by reducing the
number of rules compared to "simple rulesets" where each rule solely
consists of a source/destination IP (network) and port (range). However, these
convenient specifications are usually translated into simple rulesets which
are then installed on the firewall. Thereby, even small front-end rulesets
may already lead to a large number of firewall rules. Consider a front-end
ruleset of just 50 rules where each source, destination and service object
consists of only 5 entries. On the firewall, this ruleset expands to 6250
rules. Moreover, each update of a network object usually causes more than
a single rule to be modified.
Host based firewalling / QoS
In an environment with high, differentiated security demands, it is necessary
to install fine-grained security policies in a flexible manner. This goal
is accomplished by host based firewalling which defines security policies
on a per host basis. This scenario is also applicable to QoS where each host
is associated with a specific flow classification ruleset.
User based firewalling / QoS
A natural generalization of host based firewalling/QoS is user based firewalling/QoS.
Here, the users are required to authenticate to a server before they are allowed
to use any service. The server then activates the user's security policy depending
on the host the user is currently working on. Besides a higher level of security,
this approach reflects the mobility of users by overcoming the artificial
one-to-one relationship between user and host as assumed by host based firewalling.
Since each login and logoff operation issues a ruleset update, user based
firewalling/QoS requires both large and dynamic rulesets. This is particularly
interesting for ISPs who want to offer different types of Internet access
models, e.g. by installing a dedicated, user editable firewall/QoS ruleset
on the ISP side.
Black lists
Another application for large rulesets are black lists based on host and
service which may grow huge in certain scenarios.
Fine grained rulesets
In the context of VPN and network segmentation, it is desirable to have
full control over the different communication paths between the networks and
VPN channels respectively. This can be accomplished by defining a communication
matrix which specifies a security policy and/or QoS ruleset for each pair
of hosts, networks or groups of hosts. Depending on the number of different
communication partners and the complexity of the ruleset per pair, the total
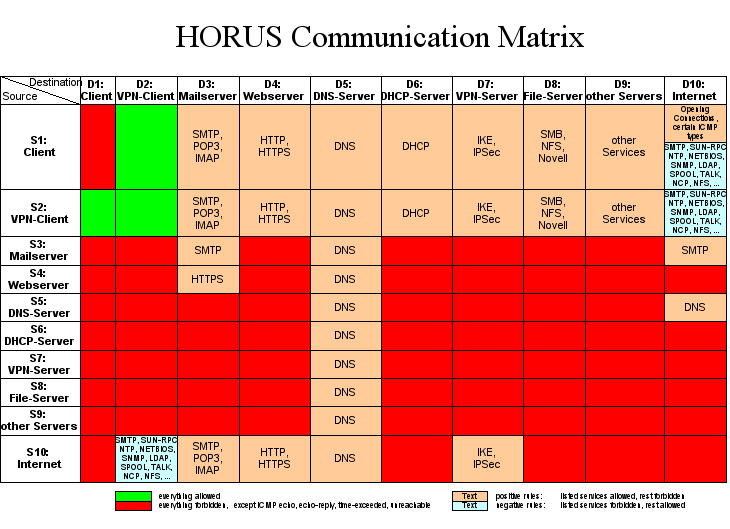
amount of rules might grow quite huge. The example communication matrix shown
below illustrates the security policy of the campus network of the Saarland
University. Assuming that each source/destination object consists of only
10 entries and the allowed services for each object pair are defined by 3
rules on average, the total number of rules implementing the policy grows
to an astonishing 30000. Despite the huge number of rules in such scenarios,
HiPAC is able to generate a compact representation of the decision data structure.
This data structure is expected to completely fit into the caches of modern
CPUs even for the largest real world setups which guarantees optimal lookup
performance.